"Should we move to the cloud?" This a common question from the C-suite for IT stakeholders. Usually, the follow-up question will be, “how secure would it be for the data and applications?” or “how much money will we save by migrating?”
There are many good reasons for an organization to move to the cloud, such as efficiency, cost, scalability, and flexibility. Among them, one of the most frequently mentioned benefits is security. Why is the cloud more secure than legacy systems? We know that those top cloud service vendors have great security infrastructure and supreme support for security. Meanwhile, legacy system security can be unreliable and difficult to implement, which makes legacy systems increasingly vulnerable to hackers. However, the complexity of migrating to the cloud includes mission-critical data, infrastructure, services, and human elements and any weak point in these parts will lead to security pitfalls. On the one hand, the organization can significantly bolster its chances of security success by moving to the cloud. On the other hand, if the organization does not leverage best practices and follow a well-executed plan, security can be compromised.
To obtain a better picture of the new security reality as companies quickly adapt to cloud environments, a study conducted by CyberCube reveals that more cloud adoption does not guarantee less data breach incidents.
This study focuses on finding the correlations between cloud services adoption (technology dependency) and cyber breach data worldwide, based on analysis of companies breached from July 2015 to June 2020.
By utilizing CyberCube's own Enterprise Intelligence Layer (EIL) dataset and conducting a stratified sampling process based on revenue distribution, three types of companies have been examined carefully. These are:
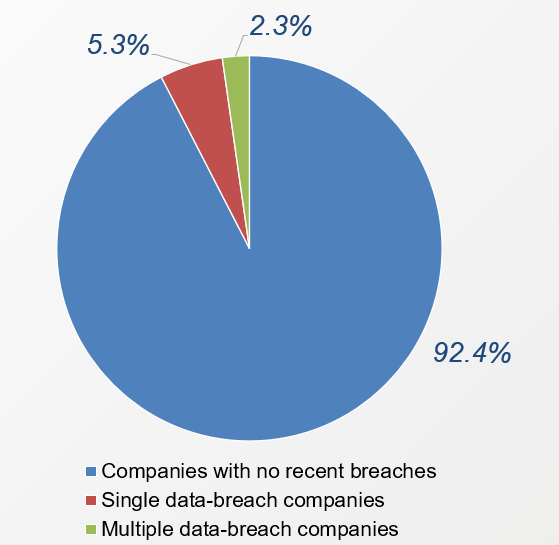
- Companies with no recent breaches: “recent” defined as having experienced no breach before July 2019.
- Single data-breach companies: suffered a first-time data breach incident during the last year (July 2019 to June 2020).
- Multiple data-breach companies: suffered multiple data breach incidents since July 2015 and at least one incident during the last year (from July 2019 to June 2020).
The pie chart shows the composition of the data we used for the study. The overall data sample size after the sample selection process is 5,409 companies.
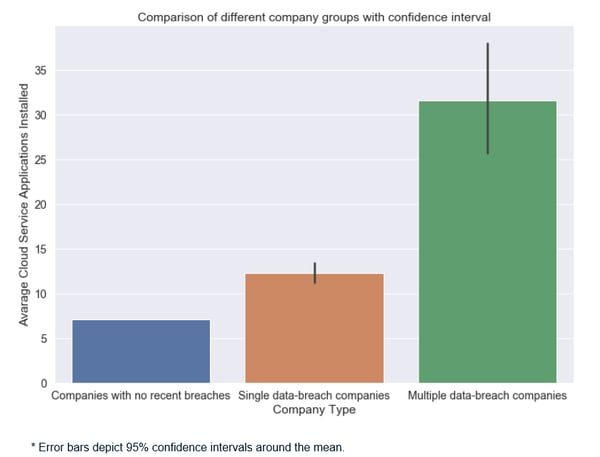
From our data statistics and a series of hypothesis tests, we found out that a) the average cloud services installation numbers are 7.1, 12.3, 31.6 respectively, and b) the mean values of each group are significantly different from each other. With the concept in mind that "correlation does not imply causation", we couldn’t conclude the cause-and-effect relationship that the higher the cloud adoption services level, the more likely a data breach is. However, we do know that the multiple data-breach companies installed more cloud service applications than others, and more cloud adoptions do not automatically guarantee less data breach incidents.
According to a survey by IDC*, more than a third of companies purchased 30+ types of cloud services in 2019. More recently, with businesses rapidly moving to the cloud to accommodate the remote working style, understanding the security challenges posed by this transition is essential for managing and mitigating risk. Fortunately, cloud security risks can be largely mitigated by following cloud security best practices, including:
- Identifying and maintaining the necessary security controls
- Understanding the shared responsibility of maintaining security between the cloud service provider and the user
- Compliance with regulatory requirements to secure data in the cloud environment.
Equally important is continually enhancing data security management by:
- Providing date security awareness for all employees
- Protecting, backing-up, organizing all data resources
- Encrypting all devices and data transition
- Establishing data access rules and monitoring abnormal signals
- Updating application passwords regularly.
Finally, cyber insurance, a very valuable risk hedging mechanism, can also help companies to mitigate the cost of a data breach by reimbursing the organization for legal fees, helping with the cost of crisis management and investigation, notification costs, extortion liability fees, and third-party damages relating to network or system outages.



