Cyber catastrophe scenarios are the modeled answers to the question: “What is the worst that can happen from a cyber attack?” As such, modelers must strike a balance between optimism (typically there is low likelihood that enough things will go wrong to cause such an event) and realism (based on historical precedent and the proliferation of capable actors and advanced tools, these events can occur).
Cyber catastrophe scenarios are a moving target; they must be revisited, refined, and updated frequently based on the changing threat landscape and new data. Both literary (narrative) and mathematical (modular) components combine to form each catastrophe scenario in CyberCube’s Portfolio Manager catalog.
Let’s take a look at the components needed to build a cyber catastrophe scenario.
The CUBE framework
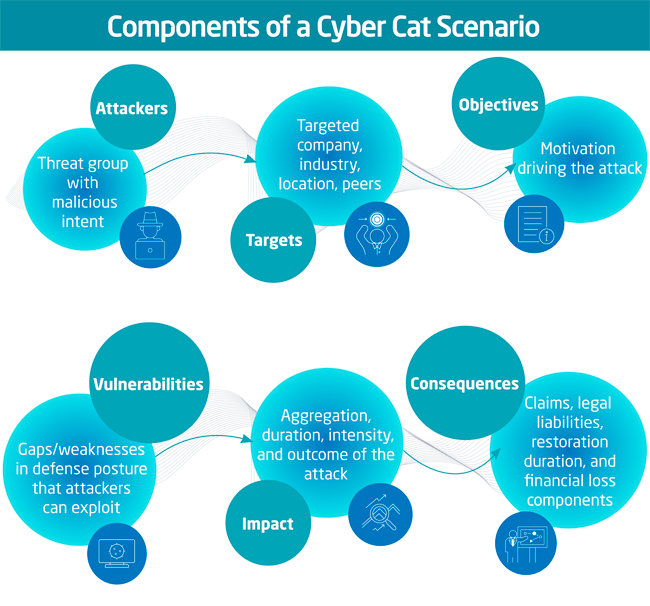
CyberCube has developed a “CUBE” framework for the development of cyber catastrophe scenarios in reference to the six key components critical to defining a modeled cyber event depicted below.
-
Attackers
Attackers are defined as a threat actor or group with malicious financial or destructive intent. Each cyber attack scenario class is developed based on an attacker from the CyberCube Threat Actor Database incorporating eight different classes of attackers.
-
Targets
Targets are Single Points of Failure (SPoFs). An insured's supply chain exposure to a vulnerable technology or service, or a SPoF, includes both technologies as well as companies within a specific industry, size and location that if targeted will achieve the maximum impact desired by the attackers.
-
Objectives
The objectives and motivations driving the attack need to address questions critical to the insurance industry, such as whether the motivation is financial or geo-political and potentially classified as an act of war. It is often not easy to classify these motivations given the support of nation states for rogue cyber groups.
-
Vulnerabilities
Attackers will target vulnerabilities in technologies and systems. The attacker’s aim is to use available tools and resources to exploit the gaps and weaknesses in the defense posture of companies in order to act upon desired objectives.
-
Impact
The impact of an attack for each scenario is assessed based on the loss aggregation potential relative to the attack footprint (the number of companies impacted), the attack duration, and the attack intensity. Key factors to consider are what companies, data or systems are impacted?
-
Consequences
Finally, the severity or financial consequences of the attack need to be assessed. This assessment reflects the insurance claims from costs such as legal liabilities, data restoration and recovery, customer notification, ransom payments, and other types of loss components from a cyber attack.
Defining plausible future cyber attack scenarios
When developing plausible scenarios, a number of considerations come into play. These include the economic and technological factors driving cyber risk, changes in the cyber insurance market, changes in the legal and regulatory landscape, the availability of high quality data, and the evolution of threat actor tactics and techniques.
A necessary addition to this foundation is a clear framework with a set of definitions and assumptions that can be applied within the context of the acceptance criteria for an aggregation risk cyber attack event. The final step is then identifying the types of plausible future events based on known or developing classes of vulnerabilities or exposures attractive to threat actors.
Defining attack scenario classes
A successful approach requires the definition of classes of scenarios relative to the type of attack threat.
Exposed data attack
A common type is an attack leading to exposed data. This includes data breaches, exposure, and theft. A large-scale data theft from an electronic health records provider is one example scenario class. An example of an attack analogue is the November 2021 GoDaddy data breach resulting in large scale exposure of email addresses and passwords for over a million customers.
Supplier outage attack
Another category is a supplier outage attack. In this type of scenario class attack, a supplier experiences long-term outage or delays, causing wide-scale business interruption and other cascading impacts. A recent example is the November 2021 Google Cloud outage due to failures in internal load balancing and CDN services resulting in disruptions to major customers such as Spotify, Discord, and Etsy.
Critical vulnerabilities
Attacks against products that have documented or undocumented critical vulnerabilities are another attack threat that can result in large scale data breach and loss. This type of scenario is similar to the 2017 NotPetya malware attack targeting critical vulnerabilities in the Microsoft Windows operating system. Another more recent event was the 2021 Microsoft Exchange Server attacks via four separate “zero-day” exploits, resulting in backdoor access to emails and passwords as well as follow-on ransomware attacks.
Business email compromise
Business email compromise is another type of potentially catastrophic cyber event with cascading impacts across companies. In this scenario, a large-scale data theft from an email service provider occurs. The 2019 Silent Starling vendor email compromise attacks involved the exploitation and compromise of targeted business email accounts to send out carefully targeted phishing emails to execute financial fraud, data theft and extortion campaigns.
Access abuse
Threat actor access to a company via its customers or suppliers is commonly termed as access abuse. An example scenario class for this type of attack threat is a large-scale cash theft, from a financial transaction provider, via a compromised customer account. The 2019 Airbus cyber attack occurred via compromised VPN access of suppliers such as Rolls-Royce and Expleo. The suppliers’ direct VPN access to Airbus was used by the hackers to gain access to Airbus’ networks with the goal of stealing data.
Product tampering
Finally, product tampering is a threat type where a product is tampered with or altered by attackers. Examples include the 2020 SolarWinds supply chain attack where a software update was injected with malicious code, and the Passwordstate password manager malicious update attack in April 2021. Another type of attack is the potential for a large-scale flight disruption to a leading airline via digital tampering of flight navigation systems.
CyberCube’s mission to define the possible
While the development of scenarios for cyber catastrophe risk models has unique and challenging considerations, a comprehensive understanding of the key drivers of systemic risk through a structured development lens can deliver the level of understanding required by the market. Real-world events can be analyzed in this context, but even more importantly, it provides the foundation needed to not just understand, but also quantify exposure to cyber catastrophic events that could happen in the future.
This three-part series of blogs — Defining the Possible — has demonstrated the various elements needed to develop credible cyber catastrophe scenarios, from what you need to consider when developing cyber catastrophe models to the criteria needed to apply to insured loss models. If you missed these parts of the series, check them out here:
- Part 1 - Considerations to account for when developing cyber catastrophe scenarios
- Part 2 - Criteria for incorporating cyber attack scenarios in insured loss models
CyberCube provides the world’s leading cyber insurance analytics and has a deep understanding of cyber catastrophe risk models. Our Portfolio Manager solution incorporates the widest array of defensible scenario classes within its model available in the market today — helping (re)insurers reliably quantify their portfolios’ loss potential, manage their risk and make profitable decisions.




