On November 17, 2021, GoDaddy discovered unauthorized third-party access to the company’s Managed WordPress hosting environment. This means that data associated with GoDaddy’s customers who rely on GoDaddy for hosting their WordPress websites were likely compromised.
GoDaddy’s incident team took action and forced the threat actor out of the company's network, but not before 1.2 million GoDaddy customers’ login credentials were stolen, putting those accounts at high risk of being targeted in business email scams and phishing campaigns.
There is also concern from security experts on the potential for stolen SSL keys and certificate issues by certified authorities that ensure the security and safety of websites. In fact, these stolen SSL keys are the biggest outstanding risk alongside phishing. SSL keys take time to be re-issued as this involves coordination with the certificate authorities. Re-issuing up to 1.2 million SSL keys could take significant time. In the meantime, attackers can use the stolen SSL keys to impersonate legitimate website domains for other attacks or engage in domain hijacking and extorting companies by demanding ransoms to get their domain back.
GoDaddy breach is another wake-up call for cyber (re)insurers
Since the attack, GoDaddy has notified the US Securities and Exchange Commission (SEC), claiming that the attack has been contained. Customers running WordPress websites on GoDaddy’s servers are receiving additional support to reset login credentials.
Although customers using GoDaddy to host their WordPress websites never experienced downtime and the attack is not guaranteed to trigger catastrophic losses, the event is yet another wake-up call to (re)insurers that large-scale cyber loss events that impact tens of thousands of companies and millions of users at the same time are indeed possible.
The GoDaddy breach further underscores the importance for (re)insurers to invest in solutions for modeling cyber attacks on Single Point of Failure (SPoF) technologies that can lead to catastrophic losses. Solutions that enable (re)insurers to map the specific SPoFs that their insureds rely on for critical workflows are also key. Additionally, cyber underwriters should look closely at this breach as a cautionary tale for what can go wrong if critical cyber security risks are not identified early.
Large-scale data breaches involving login credentials can turn into catastrophic events
Data breaches at Internet-enabling SPoF such as web-hosting providers, email services providers, certificate authorities, and domain registrars like GoDaddy can lead to the mass theft of login credentials and email addresses. This in turn puts the subjects of the stolen data at greater risk of being targeted in other attacks. In the worst-case scenario, threat actors could target all of the stolen email addresses obtained from GoDaddy with malware-laden phishing emails.
For example, in 2017 Gmail users were targeted in a widespread phishing campaign. Users received an email from a trusted contact that was also cleverly crafted to bypass email security technologies. After clicking a link in the email, the user was prompted to give permission to a malicious Google Docs App. Permission was given to the imposter app to read, send, and delete all emails as well as manage contacts — resulting in a breach of user information and email content. The worm-like malware propagated itself by spreading to infected users’ contacts.
Do (re)insurers understand their cyber exposure?
While the GoDaddy breach has yet to turn into a large-scale business interruption event, a more malicious attack, such as a targeted ransomware attack against key SPoF like GoDaddy itself, would likely result in more severe damages and unplanned downtime for GoDaddy’s customers. This scenario should have (re)insurers asking themselves if they understand their exposure when it comes to modeling the financial impact of a malicious cyber attack against critical SPoF, especially those that are considered to be the backbone of the global public Internet.
CyberCube’s solution, Portfolio Manager, aims to quantify the risk of potential SPoF attacks and cyber risk accumulation. The solution provides a wide range of possible cyber events across 29 catastrophic cyber scenario classes, such as large-scale data theft at critical SPoF including GoDaddy, which also leads to a widespread phishing campaign and the successful mass deployment of credential harvesting malware. CyberCube also helps clients model the impact on their portfolios of a mass revocation at a leading certificate authority such as GoDaddy.
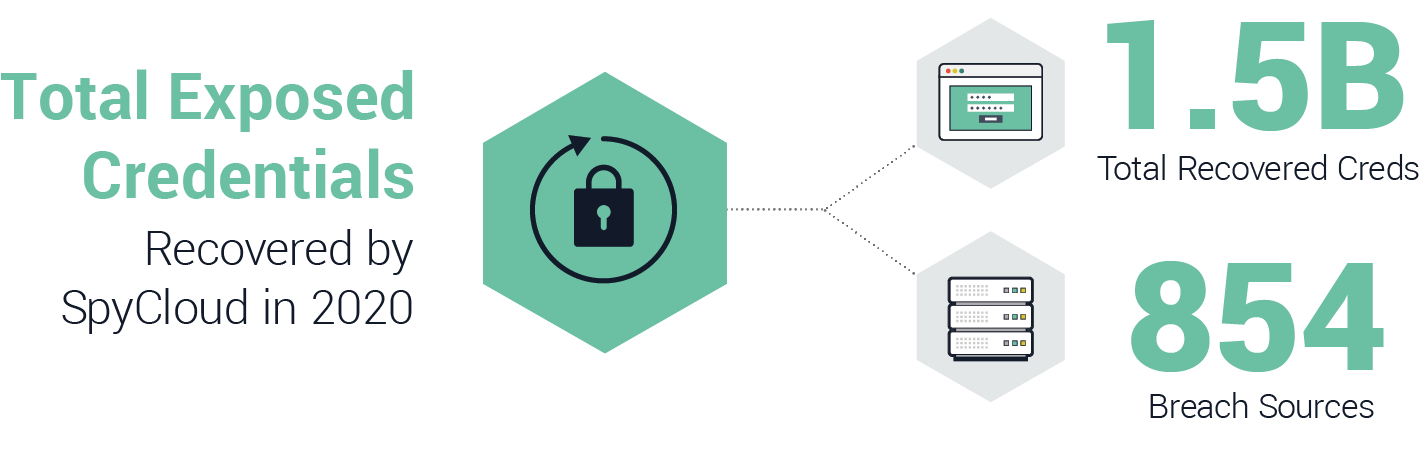 Image courtesy of SpyCloud, showing the volume of login credentials exposed online. The credentials stolen from GoDaddy could land on the Dark Web where they may be sold at auction.
Image courtesy of SpyCloud, showing the volume of login credentials exposed online. The credentials stolen from GoDaddy could land on the Dark Web where they may be sold at auction.
GoDaddy is a Single Point of Failure (SPoF)... and so is WordPress
As we discussed in a recent report, a SPoF is the targeted entity in a digital supply chain for a given attack scenario that has multiple dependent and interconnected entities. Note: the SPoF in a given attack scenario may or may not itself be present in a (re)insurer’s portfolio.
GoDaddy is one of several leading domain registrars that also offers website and email hosting, among other products and services. In particular, GoDaddy offers the ability to host WordPress websites on its servers. GoDaddy’s WordPress customers’ data comprised the majority of the credentials stolen in this attack. These companies are most at risk of having their email addresses targeted. (Re)insurers can turn to CyberCube for help with identifying accounts that are at risk.
CyberCube’s SPoF Intelligence tool can help (re)insurers identify insureds that are reliant on vulnerable SPoF such as GoDaddy.
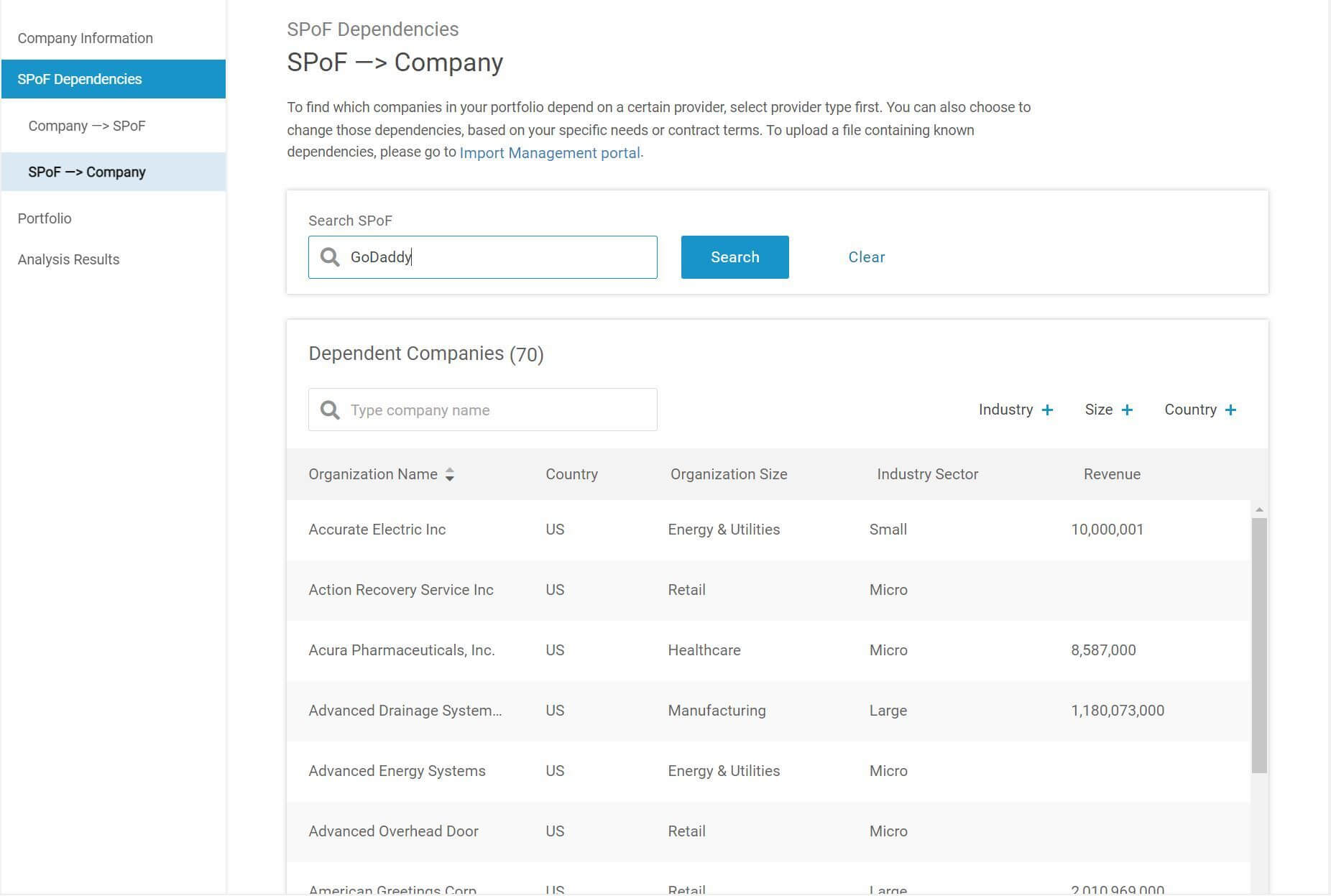 In the sample analysis above, CyberCube’s SPoF Intelligence solution found that 70 insureds are dependent on GoDaddy.
In the sample analysis above, CyberCube’s SPoF Intelligence solution found that 70 insureds are dependent on GoDaddy.
GoDaddy is a SPoF with myriad security risks
Cyber underwriters should look to GoDaddy as a warning for the types of high-risk cyber security signals to look out for when deciding on whether or not to underwrite an account.
GoDaddy disclosed to the SEC that the breach emanated from a threat actor using a “compromised password” to access the code base for its Managed WordPress environment. It is possible that the threat actor obtained an exposed login credential for GoDaddy from a leaked database on the Dark Web. In fact, CyberCube’s single risk cyber underwriting solution, Account Manager, flagged a high risk of “Exposed Credentials” for GoDaddy prior to this latest breach. GoDaddy was observed as having over 270 different exposed records in the last 60 days including email addresses, and combinations of passwords and emails that can be used to login to the company’s network.
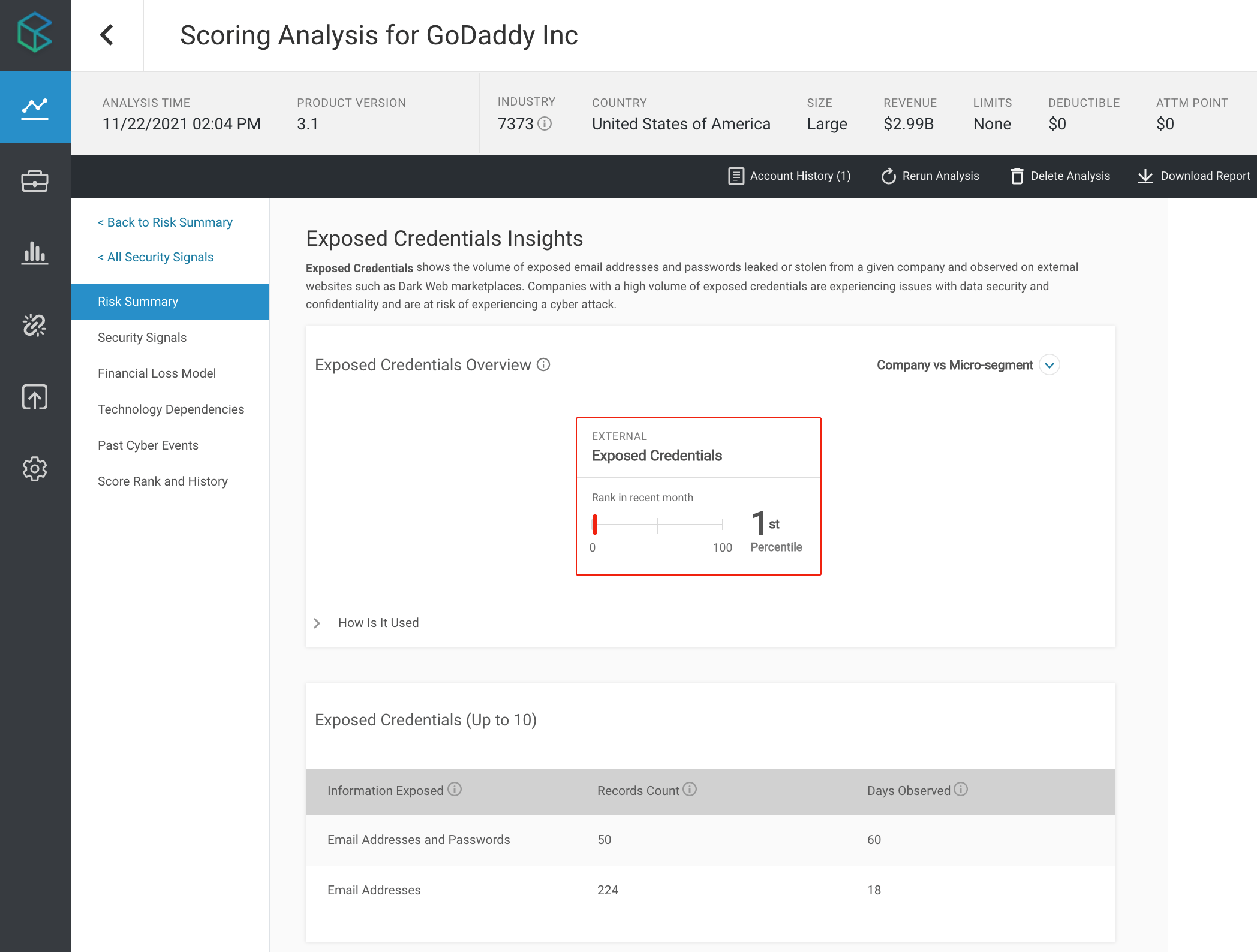 In the analysis above, from the Account Manager solution, GoDaddy is observed having over 270 exposed records in the last 60 days.
In the analysis above, from the Account Manager solution, GoDaddy is observed having over 270 exposed records in the last 60 days.
In addition to Exposed Credentials, GoDaddy is dealing with other high-risk security issues. CyberCube’s data shows the use of End-of-Life Products on GoDaddy’s network including various deprecated Microsoft products that are unpatchable and vulnerable to exploitation. CyberCube’s data also shows evidence of known malware families including the infamous credit card skimming malware known as Magecart on GoDaddy’s network.
Perhaps most concerning are CyberCube’s observations of high-risk ransomware signals at GoDaddy, including Ransomware Vulnerabilities and RDP Open Ports (two of the most common ransomware threat actor infiltration vectors), Ransomware Toolkits (a precursor malware that leads to ransomware), and the presence of known Ransomware Infections such as the Sodinokibi strain, often used by the prolific ransomware-as-a service operator REvil.
GoDaddy’s security issues are indicative of the company’s inherent exposure to cyber threats as well as a deficiency around remediating active threats on the company’s network. GoDaddy is a heavily targeted company. It is not surprising that top 1% threat actors like Magecart and REvil have been spotted on the network. Nevertheless, underwriters that effectively assess these risks in context are in a better position to decide whether or not to underwrite the account.
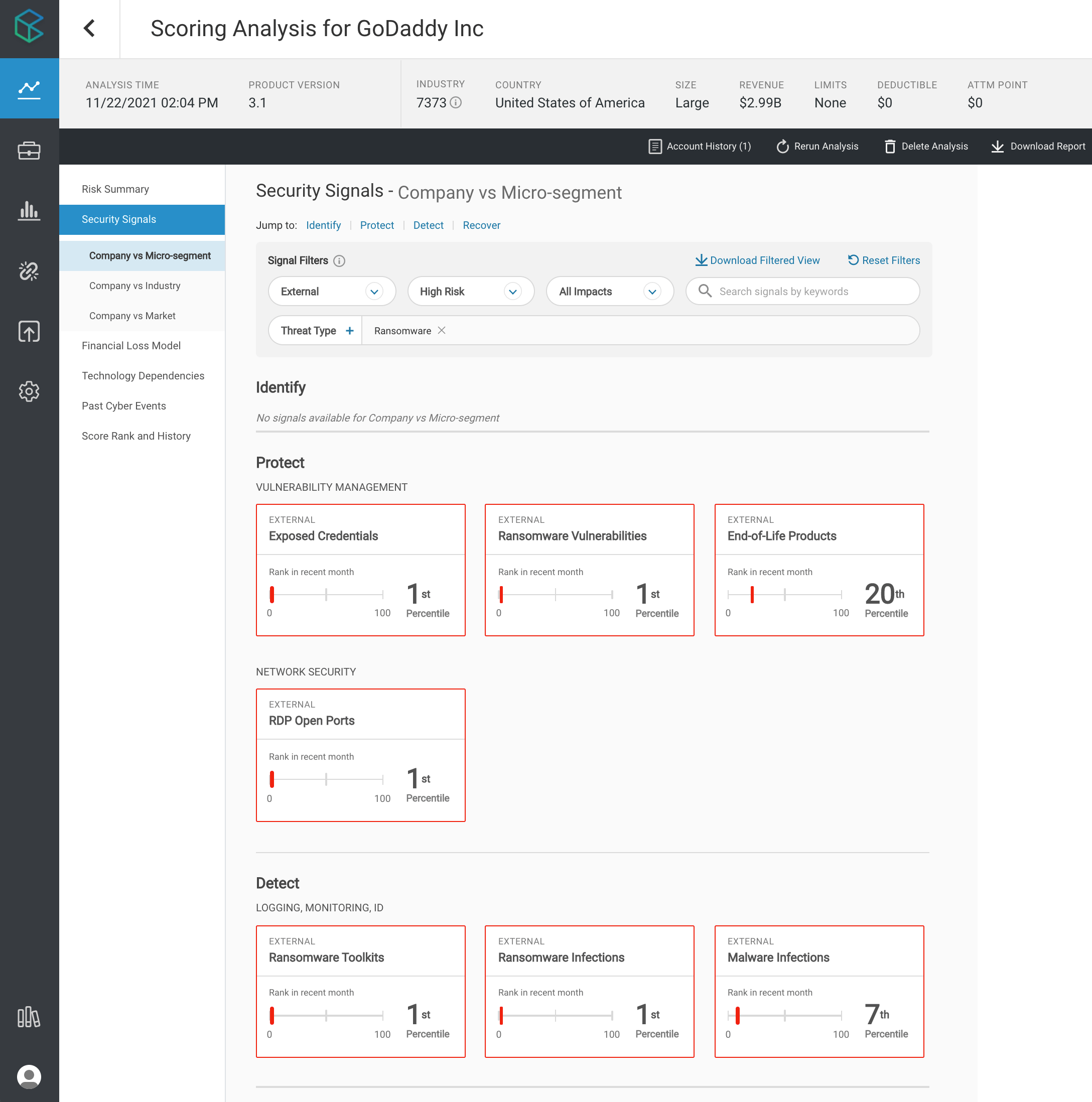 In the analysis above from Account Manager, GoDaddy is observed with seven high-risk ransomware threat signals.
In the analysis above from Account Manager, GoDaddy is observed with seven high-risk ransomware threat signals.
Account Manager allows underwriters to view an account’s disclosed cyber events. CyberCube data shows that GoDaddy has been targeted in at least 14 separate data breaches involving PII records since 2011, as shown below.
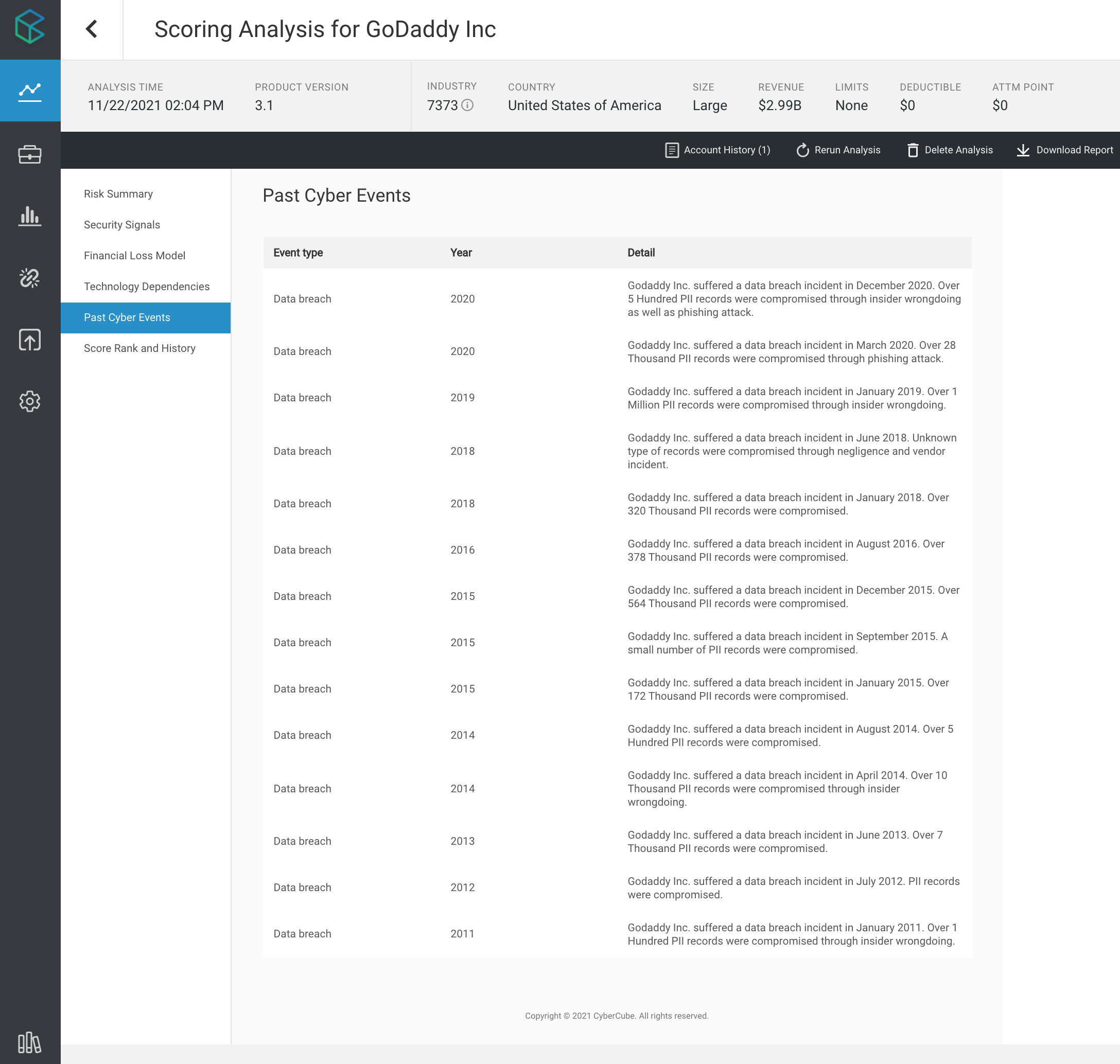
CyberCube anticipates GoDaddy is likely to be targeted again in the future. The critical nature of the company’s business for enabling large swaths of the Internet makes GoDaddy an attractive target for cyber threat actors.
Expect more SPoF cyber attacks and outages
GoDaddy is only the latest alarm bell to sound a warning to (re)insurers of the cyber risk inherent in SPoF technologies and companies. Following recent cyber attacks on SPoF including (but not limited to) SolarWinds, Microsoft Exchange, and Colonial Pipeline, it should now be abundantly clear to (re)insurers that SPoF cyber attacks with catastrophic scope are increasingly possible.
CyberCube expects to see a range of cyber threat actors including criminal ransomware operators and their affiliates, as well as nation-state sponsored actors targeting SPoF technologies and companies in coming years. All insurance industry stakeholders ought to remain vigilant and prepare themselves to adequately assess SPoF-related cyber security risks.
If you’d like to learn more about how cyber risk analytics tools can identify future SPoF attacks, you can get in contact us at CyberCube today. Our CyberCube Concierge service can also advise your team regarding the cyber threat landscape and how to best manage your cyber risk.