By definition, cyber attack scenarios are developed based on their potential to depict systemic financial aggregation events impacting multiple insureds. The significant insurance loss includes both affirmative and non-affirmative cyber claims potential, though for non-standalone cyber insurance policies it can be useful to have a non-affirmative view of cyber risk. How you go about selecting scenarios to incorporate can impact the transparency, defensibility, and robustness of the model.
In this blog, Part 2 of Defining the Possible, I’ll discuss some of the criteria CyberCube uses when incorporating cyber attack scenarios into our insured loss models.
Cyber attack scenario acceptance criteria for inclusion in models
Each cyber attack scenario should be defined in the context of a genuine and plausible cyber attack relative to its impact on the confidentiality, integrity and/or availability (commonly known as the “CIA triad”) of data or systems. There must also be a clear, demonstrated adversarial motivation for the scenario attack. This includes financial, geopolitical, disruptive or hacktivist motivation, which contrasts with inadvertent human actions or mistakes that can cause disruptions with significant financial losses.
The development of cyber scenarios with aggregation potential requires data that address the following four key forces driving systemic cyber risk today:
1. Dependency on a few major players such as technology giants for core internet, software, and networking and infrastructure services
2. Increasing supply chain complexity reflected by increased outsourcing and embedded dependencies in technology products and services
3. Growing cloud and open source software (OSS) adoption bringing challenges of configuration and vulnerability management as well as resiliency in the face of an outage
4. Expanding threat actor capabilities with a growing global dark web market for hacking tools and services bringing challenges to law enforcement to effectively combat cyber crime
As the technology landscape evolves in almost every line of business, the market is experiencing the increasing dominance of a few companies. An example includes the rise of Internet giants such as Amazon, Akamai and CloudFlare. They have a large footprint of interconnected and independent companies reliant on their technologies. An attack against a vulnerability in a SPoF technology or service provider could have global implications. In addition, the increasingly complex global supply chain presents opportunities for scaled weak points of entry and access that can be exploited by threat actors to reach a target.
The increase in cloud and open source software adoption is another driver of systemic cyber risk. Vulnerabilities in open source software have been a leading exploit for threat actors given the potentially large footprint impact for this type of SPoF. Similarly, as more organizations migrate to using the cloud (whether public, private or hybrid), this becomes an increasingly vulnerable and targeted class of SPoFs.
Finally, the threat actor capabilities across the cyber threat landscape are expanding. This is due to several factors, including the rapid evolution of the cyber attack in a service economy where unskilled actors can purchase attack capabilities or tools in order to carry out their intent. Additionally, nation states developing cyber capabilities are using the dark web market to conduct their attacks and grow their cyber capabilities to move closer towards being developed cyber nation states.
Drivers of cyber aggregation risk
Key drivers of risk affecting the four forces for future systemic aggregation risk mentioned above are shown in Exhibit 1 in the context of historic events.
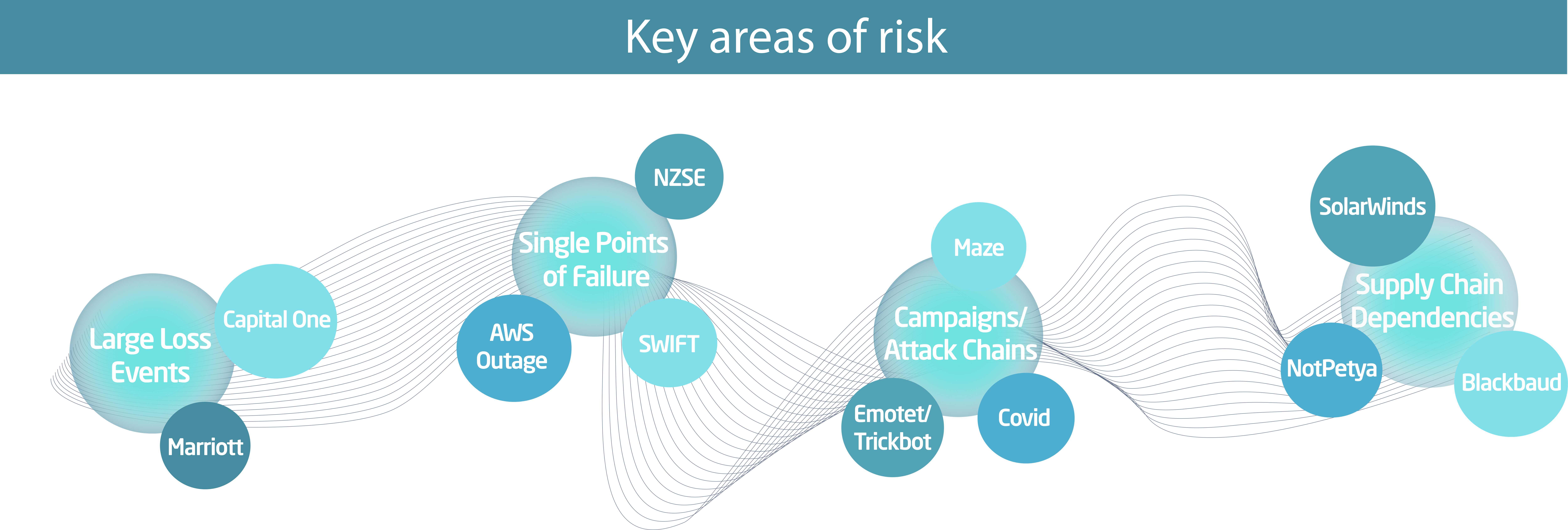
While history is not necessarily the predictor of the future of cyber attacks, past events are critical to informing trends as threat actors learn from current methods and techniques. For example, large loss breach events such as the ones deployed against Capital One, Magellan Health, the Accellion File Transfer application and Marriott impacted multiple companies with large scale data exposure.
Campaigns and attack chains (in which a series of cyber attacks are concurrently instigated against similar targets carried out by a single or coordinated threat actor group) have large scale impacts. This includes botnet attacks like those attributed to Emotet, associated malware strains that resulted in the deployment of malware and associated ransomware to hundreds of thousands of devices over several years and the Maze ransomware campaigns in 2020 with a second component of data extortion. Coordinated attacks can also take advantage of rapid changes, resulting in large scale exposure to vulnerabilities, such as the rapid switch to working from home during the COVID-19 pandemic.
Attacks via a SPoF that cause widespread impacts to a significant number of dependent companies, resulting in significant business interruption is an increasing large-scale risk. These include the New Zealand Stock Exchange denial of service attack, cloud outages like the Azure outage, and other product and service outages, such as the Garmin outage. The Microsoft Exchange attack is an example of a series of severe vulnerabilities in the Microsoft Exchange email server product, enabling threat actors to conduct attacks at scale against many companies.
Another set of risks are supply chain dependencies such as a 2020 ransomware attack that impacted hundreds of educational and non-profit companies through their supplier and service provider Blackbaud. NotPetya and the SolarWinds attack, in which many government and private sector organizations received a malicious software update through an I.T. management product, are additional examples of supply chain dependencies on vulnerable technologies.
Cyber attack scenario development lenses
In this context of multiple drivers of the risks highlighted above, CyberCube utilizes multiple lenses to develop cyber attack scenarios for loss modeling purposes. These include:
- “Rear view mirror” assessment of historical incidents to identify large impact attack trends. Similarly, it is valuable to assess past events with plausible alterations to the attack vector and review what the potential impact could be.
- Exaggeration of the present for potential changes in model assumptions that impact attack frequency and severity. An example is the February 2021 Silver Sparrow malware which infected thirty thousand Macs but did not install a malicious payload. In essence, real world cyber incidents can be used as analogues to future modeled cyber catastrophe scenarios. Working with security researchers, proof of concept attacks are analyzed to understand what the potentials are for future attacks. Even the review of influential and popular works of fiction that can inspire attackers to conduct future attacks is used.
- Exploit driven attack lens that analyzes current exploits available on the market that attackers are actively using. This analysis includes assessing what tools threat actors have developed to target and attack specific vulnerabilities. It also includes the assessment of what types of technologies attackers can exploit relative to the increasing interconnectedness of companies and their technological dependencies to increase the impact potential.
- Physical to cyber assessments, or the study of the evolution of large-scale crime and war tactics from the physical to the digital realm. As an example, criminal organizations are transitioning to ransomware tactics via digital financial extortion schemes. The rapid evolution of both technology and cyber attack software “as-a-service” markets require forward-thinking development of scenarios.
- Technology trends for both current and new technologies that will potentially evolve to impact the cyber threat landscape. Example technologies include IoT, AI, blockchain (and cryptocurrency), 5G, and quantum computing.
- Skewed distribution analysis of the top targets in the threat landscape that have a high degree of assets, brand reputation, or footprint, which would be of high interest to threat actors. This analysis focuses (skews) the analysis on the types of systemic loss attacks most likely to result in a catastrophic loss.
Understanding the evolution of cyber risk
In this blog, Defining the Possible Part 2, I’ve broadly identified the array of criteria CyberCube considers when incorporating scenarios into our insured loss models. However, the unique nature of cyber risk and the way it is constantly evolving makes it fundamental that scenarios are frequently reviewed and modified.
At CyberCube, we have years of experience in building catastrophe scenarios, so we understand what needs to be considered, and our multi-disciplinary team of cyber security experts, underwriters, actuaries, data scientists, and cyber risk modelers is continually refining and updating our approach to deliver a robust, transparent model. Our solution, Portfolio Manager, provides access to the industry’s broadest array of cyber catastrophe scenarios, making it easy to comprehensively and defensibly assess your loss exposure.
Check out the third and final blog in the Defining the Possible Blog series — 6 components to developing a cyber catastrophe scenario — where CyberCube’s Senior Cyber Risk Modeler, Charlotte Anderson, will discuss the steps CyberCube takes to develop a cyber catastrophe scenario.
If you haven’t already read it, the first part of the Defining the Possible blog series can be found here — Considerations when creating cyber catastrophe scenarios.
If you’d like to learn more about cyber catastrophe scenarios, check out our free report — Designing a Cyber Catastrophe.
.png)



