Current State of Ransomware
This year we have observed the bear’s share of the ransomware market consisting of two main approaches: the ransomware-as-a-service (RaaS) pool, mainly composed of ransomware developers and affiliates who infect systems (for example, REvil/Sodinokibi), and the “big game hunting” pool which leverages already compromised networks (usually by Emotet and/or Trickbot) to launch highly targeted attacks on valuable targets (for example, Ryuk). But we should ask ourselves, are these the only successful approaches or do others exist?
A New Play?
Let’s step back for a second and consider: in an ideal world where everybody has backups and can easily deploy them, can ransomware operators blackmail victims? Despite being far from this ideal world, for years operators have thought about additional “incentives” (or rather, threats) to encourage ransom payment. The most notable was claims to have stolen a copy of all of the victim’s files before encrypting them, which in turn would be published online if payment was not submitted. However, in the past, this claim has been more of a bluff than a reality. An example is the Chimera ransomware, which in 2015 made these claims, but analysis of it ultimately demonstrated files were not stolen.
The Bluff is Called
In late November 2019, an actor made similar claims when infecting Allied Universal with the Maze ransomware. The ransom demand amounted to 300 bitcoins (~USD 2.3 million at the time), but was not paid by the deadline specified by the attackers. The attackers then published 700 MB of files which appear to be legitimate files belonging to Allied Universal.
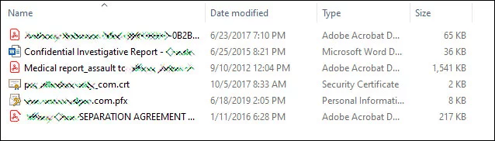
Pictured above: Partially redacted screenshot of alleged leaked files.
Recently, the actors behind the Maze ransomware published a “shaming site”, which so far lists eight companies which were infected and did not pay the ransom. The site will allegedly be used to publish stolen files, although at the time of writing, none appear available.

Pictured above: Partial screenshot of the "shaming site" allegedly published by the actors behind Maze ransomware.
Established Players Joining
A cybercriminal responsible for managing the REvil/Sodinokibi RaaS recently posted on a popular Dark Web forum stating that there are plans to start using stolen files as leverage to encourage victims to pay ransoms. Contrary to previous actors who typically reason that publishing stolen files impact victims by way of reputational damage (confirming a breach on the victim) and/or sensitive documents being exposed, the REvil/Sodinokibi crew makes the case that publication of stolen files may trigger GDPR fines on victims, which would be significantly higher than the ransom demand.
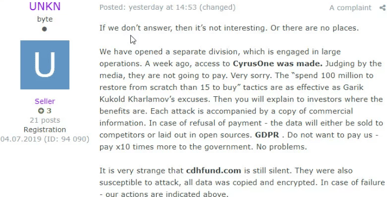
Pictured above: Post made by REvil/Sodinokibi operator.
While this is concerning, only time will demonstrate if this addition to ransomware operations is sustainable enough to become the new standard. Nonetheless, for the time being, it marks a rising trend with both new and established players.